Hmmm. I’ll check for that, but I think it was done. In a couple of cases, they asked for more information, which I provided.
Other than the requests for further validation documentation, I see no emails. What should it look like?
IIRC, they requested the information in the Azure “Identity Validation” window. But also sent to the registered e-mail address (you have to provide two different e-mail addresses, but with the same domain you own).
For example:
Action required: Complete your identity validation process
This email is to notify you that you need to complete the identity validation request for Friedrich Linder within subscription ID 87ab9da5-5ca1-487c-63b5-3d23d73fc1b5 .
Required action: Please complete the identity validation process.
Nope, at no point did I receive anything like that, on any of the email addresses that were associated with the requests. I did receive emails requesting more information, but nothing else. ![]()
This is what I documented in the original post of this thread
Mine looked like this:
Hello,
We need to verify your email address.
Thanks for your interest in Trusted Signing service’s public identity validation. As part of the identity validation process we need to verify your email address. By verifying your email, you attest to being authorized to conduct verification on your business’s behalf. A record of this attestation will be kept for regulatory purposes
Mine was identical.
Sender was
Microsoft Vetting Services [email protected]
70 minutes later, an email from
Microsoft Azure [email protected]
like what Mark quoted, saying
We’re notifying you about your Trusted Signing identity validation status
This email is to notify you that the identity validation status for Beach Bunny Software (Subscription ID xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx) has been updated to Validation Pass status. To view additional details about the status, go to the Azure portal.I definitely did an email verification process, when I first went through as Mark Goldberg documented. The last time we tried it, we realized that we already had a presence on Azure (through our Exchange usage), so we restarted the Code Signing steps. It definitely knows I exist, but has been into “limbo” mode for days. I just wish there were some way to determine the actual state of the process, and how I might talk to for assistance. ![]()
After weeks of multiple failed attempts, I finally managed to get an identity validated. ![]()
Given everyone who builds an installer needs the signing credentials, I added a new user for that.
The next hurdle was unrelated cached credentials on our build server. There are many methods that it can use to validate the identity, so I needed to disable all of those, except InteractiveBrowserCredential and SharedTokenCacheCredential, resulting in this metadata.json:
{
"Endpoint": "https://wcus.codesigning.azure.net/",
"CodeSigningAccountName": "CodeSigningInstance",
"CertificateProfileName": "CodeSigningCert",
"CorrelationId": "",
"ExcludeCredentials": [
"EnvironmentCredential",
"WorkloadIdentityCredential",
"ManagedIdentityCredential",
"VisualStudioCredential",
"VisualStudioCodeCredential",
"AzureCliCredential",
"AzurePowerShellCredential",
"AzureDeveloperCliCredential"
]
}
I actually disabled everything except interactive first, then noticed that it never used the newly cached credentials, so I reincluded SharedTokenCacheCredential. Therefore, there’s a chance that our new credentials overrode some cashed credentials for something else. No one could recall what that might be, though, and this AWS EC2 instance was used for something else before being repurposed as a build server, so we’re probably safe.
Things are finally working, a month after beginning it all. ![]()
My first try started August 19, 2024 and failed on September 23, 2024 (5 weeks).
Second try took from November 2nd - November 14 (success). Two organization and one individual Trusted Signing certificates.
Trusted Signing is the best thing since sliced bread, IMO.
Friedrich
My comodo cert expired in few days. I’ve followed instructions here and with .cmd file successfully signed my app. Friedrich, can we use MS signing inside SB 2023 or we have to wait until SB 2025?
I don’t fancy buying comodo again for 300+ usd if MS works for much less ![]()
Thanks
Bostjan,
please wait another 2-3 days. I’ll make the official SetupBuilder 2025 BETA available very soon. It’s all built-in, including download of the required signtool & dependencies (for 32- and 64-bit Windows). It’s point.click.sign with SetupBuilder 2025 ![]()
Friedrich
And… please DO NOT buy certificates from the cartel (Sectigo, etc.) ![]() Microsoft Trusted Signing is a game changed, IMO.
Microsoft Trusted Signing is a game changed, IMO.
Awesome, thank you, Friedrich!
Quick update: this weekend we’ll complete the last new feature in SetupBuilder 2025 BETA. Then we are feature complete and ready for the public BETA test.
This is a HUGE update focusing on a massive rework of the underlying installation framework and adding state-of-the-art new features.
More to come soon…
Friedrich
Last (I hope) SetupBuilder 2025 pre-BETA version released to selected users (with SafeNet eTokens) today.
We plan to send out BETA invitations to all registered SetupBuilder uses this week.
Friedrich
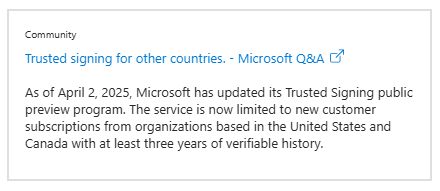
Ouch ![]()
To all US and Canada-based Clarion-developer “organizations”… I would strongly suggest to try to get your hands on a Trusted Signing certificate. This really is a game changer.
To be on the safe side, I still have EV eToken and EV Cloud certificates. Without a code-singing certificate, it’s almost impossible to distribute software to end-users today.
I re-registered my lindersoft license today. I am waiting for my ID to download the new version. In the meantime. Should I follow marks instructions to get my certificate started or should I wait? Do you have similar instructions in the lindersoft help?